PROVIDENCE – Cybercriminals are becoming more lean, fast, abundant and strategic, and they are evolving from a nuisance to a “clear and present danger,” said a cybersecurity expert who delivered the keynote address Thursday at Providence Business News’ Cybersecurity Summit in partnership with the Tech Collective.
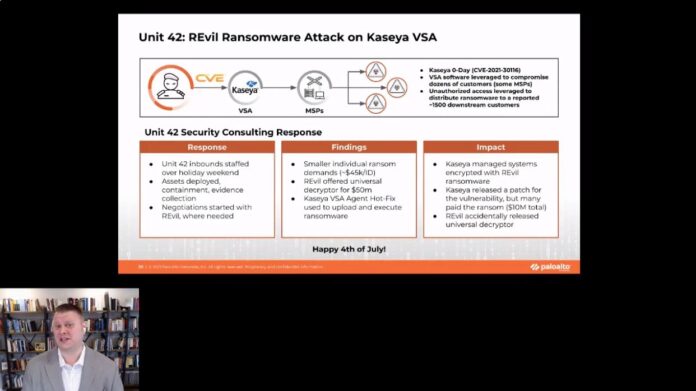
Dan O’Day, director of Unit 42 by Palo Alto Networks, presented to an online audience of businesspeople a description of cybercrime that was chilling in part because of the ease with which hackers can get into the game.
“Organizations are getting hammered” by four common forms of attacks by criminals demanding ransom, O’Day said. The four formats are encryption, where the attacker locks a victim organization’s data until a ransom is paid; data theft, where the attacker threatens to release private data; denial of service, where the attackers may shut down a company website or communications with workers; and harassment, where the attacker pummels the victim organization with threatening voicemails and other forms of harassment.
The keynote was part of an extensive event Thursday that included two breakout panels of experts, a discussion of the concept of “zero trust” by Todd Knapp, founder and CEO of Pawtucket-based Envision Technology Advisors LLC, and closing remarks by R. Michael Tetreault, cybersecurity adviser for Rhode Island, Region 1 New England in the Integrated Operations Division, Cybersecurity & Infrastructure Security Agency of the U.S. Department of Homeland Security.
One breakout panel emphasized the importance of building training and security sensitivities within organizations. Members of the panel titled “How to build a culture of shared responsibilities in your organization” all emphasized the idea that risks of attack and responsibility to protect against cybercrime stretch across the entire organization.
“Security is not only an [information technology] problem,” said Tony Faria, chief information security officer and security strategist for Consortium Networks in Boston. “Cyber crosses all corporate risks; everything can be impacted.”
People are “the weakest link and the strongest asset,” in protecting a company from cybercrime, said Cindy Lepore, vice president, client adviser, Marsh McLennan Agency LLC. Answering a question for the audience, she said insurance carriers have many resources for businesses trying to mold employees’ attitudes and practices toward cybersecurity.
Other participants in the shared responsibilities panel included Jason Albuquerque, chief operating officer at Envision Technology, and Jon Fredrickson, certified information security manager, chief risk officer/corporate affairs at Blue Cross & Blue Shield of Rhode Island.
Perhaps most disturbing of O’Day’s descriptions was how easy it is for bad actors, which may include individuals, nation-states, criminal gangs or others, to get into the business of lawbreaking through the internet.
“The business model is becoming more lucrative, and it is easy to get involved,” O’Day said. In fact, there are businesses that provide all the mechanisms and tools a hacker needs to get started, such as infrastructure, exploit kits and storage service. The individual hacker, in effect, becomes an “affiliate” in the business model, O’Day said.
“The bar is lower for people to get involved” in doing cybercrime,” O’Day said. “All the infrastructure is provided by the overarching organization.”
In 2021, O’Day said, that average ransom paid out has been $570,000, which was 82% higher than the previous year.
Costs for businesses to routinely defend themselves from attackers or to recover from a ransomware attack are enormous. Preventive costs may include cyberattack insurance premiums and IT support. Costs after an attack could include IT work, crisis communications, recovery of software and hardware, loss of business productivity, professional negotiator services, brand protection and – possibly – paying the ransom.
People who perpetrate these crimes have gotten help in in the last 19 months by the pandemic, which caused many people to migrate to home offices, thereby increasing weak points across millions of home computers, many with lax protections. The pandemic also caused businesses to move work to the cloud, which is vulnerable.
In a second breakout session, panelists shared steps employers can take to reduce security risks when they have a remote workforce.
In the early days of the pandemic, many employers scrambled to allow remote work, with some assuming it would be a short-term measure. But as businesses realize that employees see remote work as a perk, companies need to adjust to “a permanent change in the way they work,” said Eric Shorr, president at Secure Future Tech Solutions in Warwick.
With remote work and a wider platform to cover comes increased security risks, according to the panelists. An employee may have devices in their house that can be hacked, lack the means to properly dispose of sensitive information or work on a shared WiFi network, among other security risks.
While employees “don’t want to be your weak link,” said Linn Freedman, chair of the data privacy and cybersecurity team at Robinson & Cole LLP, employers must take extra precautions to decrease security risks.
To reduce risk, Freedman advised employers to take extra time to educate employees on extra security measures they can take, like using a private WiFi network and turning off camera devices, such as an Amazon Alexa, when they’re working from home.
Employers can also reduce risk by providing employees with company devices, such as laptops, said Daniel Andrea, a partner and director of information systems at Kahn, Litwin, Renza & Co. Ltd. in Providence. Businesses can encrypt and regulate these devices to prevent users from installing potentially unsafe software or printing sensitive materials.
Additionally, he said, if employees are allowed to print from home, companies should provide a paper shredder so they can properly destroy information.
Panelists also emphasized multi-factor authentication as a powerful tool against security breaches.
The panel also included Anthony Siravo, chief information security officer at Lifespan Corp., and John Sullivan, executive vice president and chief information officer at BankNewport.
In a closing session, Knapp encouraged businesses to adopt “an overarching way of thinking about and looking at the security of your environment.”
Cybersecurity “is your top priority as a business professional, even if it isn’t your primary job,” Knapp said. “It’s something we all have to be worried about.”
In final remarks, Tetreault said that senior leaders also need to understand cyber risks and plan proactively.
While measures such as cyber insurance are helpful, employers must take extra steps to fight cyberattacks, Tetreault said, such as educating other senior leaders and providing up-to-date training for IT professionals.
While “we prepare not to be attacked,” Tetreault said, companies must also ask: “When a bad event happens, how can we respond and recover?”
PBN Staff Writer Jacquelyn Voghel contributed to this report.
Mary Lhowe is a PBN contributing writer.












